EchoMark
Open siteOther
Introduction
Ultimate shield against data leaks
EchoMark Product Information
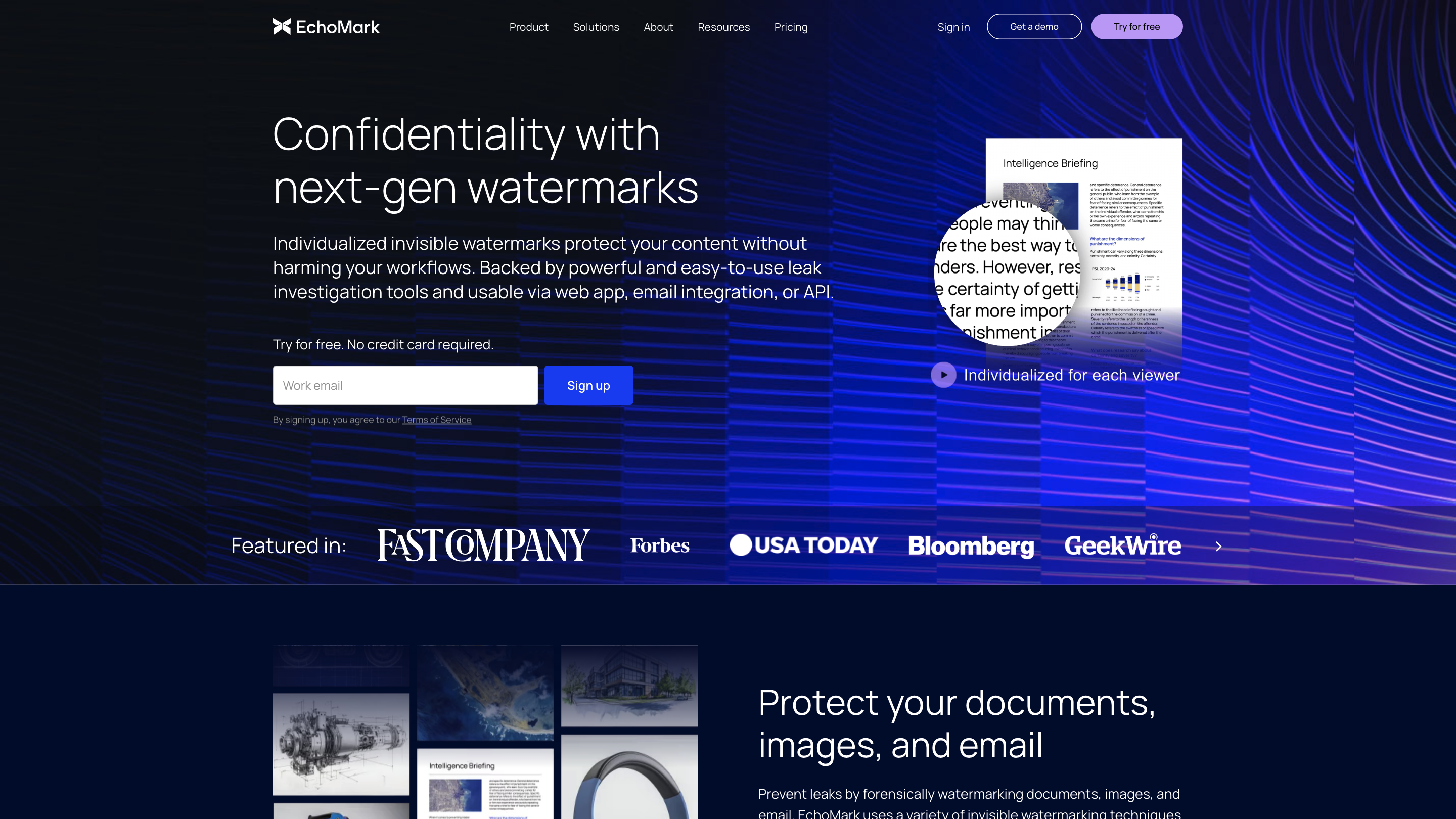
EchoMark: Protects Organizations from Insider Risk & Data Leaks
EchoMark provides next-gen invisible watermarking and leak investigation tools to prevent and remediate data leaks across documents, images, and emails. It enables individualized, invisible watermarks for recipients, leverages forensic watermarking, and offers secure viewing via SecureView links, email integration, or API. The platform emphasizes fast leak detection, precise attribution, and seamless workflow integration for sensitive communications such as M&A, HR, and strategic documents.
Key Capabilities
- Forensic, individualized invisible watermarks on documents, images, and emails
- Dynamic image watermarking with two watermark types: Chroma (invisible) and Luma (visible in print/photo contexts)
- Secure sharing via SecureView links with access controls and DLP alignment
- Tracking and analytics: see when and where recipients view content and revoke access if needed
- Leak source tracing using computer vision and watermark matching
- Lightweight, fast setup with web app, email integration, or API
- Content protection backed by investigative tools to quickly identify leaks
How It Works
- Watermark and Secure Sharing: Upload content (documents, images, emails) and apply individualized invisible watermarks. Share via SecureView links or integrated email/workspace solutions.
- Recipient Access: Recipients view content through secure channels without requiring account creation.
- Leak Investigation: If leaks occur, upload the leaked content to EchoMark’s tools. The system uses computer vision to compare against watermarked copies and generates a report indicating the likely source.
- Prevent and Revoke: Track viewing activity with analytics and revoke access as needed to minimize risk.
Use Cases
- Protect confidential documents, images, and emails across mergers, HR, and financial scenarios
- Deter data exfiltration with embedded invisible watermarks and precise access controls
- Integrate with Exchange and Workspace for seamless workflow
Security and Compliance Considerations
- Invisible watermarking provides traceability without altering user workflows
- SecureView link-based sharing supports strict access control and DLP alignment
- Detailed viewing analytics help monitor content exposure and accountability
Core Features
- Individualized invisible watermarking for documents, images, and emails
- Forensic watermarking to trace leaks to the source within minutes
- Dynamic image watermarking with Chroma (invisible) and Luma (print/photo detectable) options
- SecureView link-based sharing with access controls and DLP integration
- View analytics: see who accessed content, where, and when; revoke access if needed
- Leak investigation tools with computer vision and source tracing
- API, web app, and email integration for flexible deployment
- Partner ecosystem and enterprise-friendly deployment options